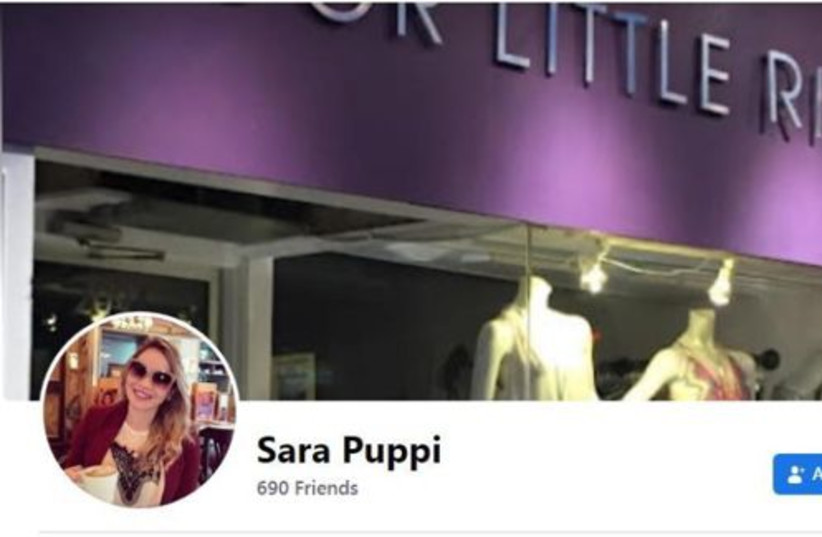
Iran has been using a phony Facebook profile under the name of “Sara Puppi” in an attempt to gather intelligence and harm Israelis, the Shin Bet (Israel Security Agency) revealed on Monday.
The Iranian operator of the fake account introduced herself as a young Jewish girl with connections and business in Israel. (Female pronouns are being used here, although the gender of the account operator or operators is unknown.) The account added thousands of friends in a very short period, most of whom were from Israel. The Shin Bet had been monitoring the account since it was created.
After speaking with targets on Facebook, the Iranian operator would get the victim to switch to WhatsApp.
According to the Shin Bet, Iran and its proxies have increasingly focused on contacting Israelis through the Internet in order to recruit them to gather intelligence and conduct terrorist activity.
The Iranian operator behind the Sara Puppi account asked her operatives in Israel to locate information about Israelis in whom Iranian intelligence was interested, without being aware that she was speaking with Shin Bet operatives.
The fake persona asked what she thought was her Israeli operative to gather information about Israeli figures and assessed the operative’s willingness to harm them. The Iranian operator exerted pressure and promised to pay thousands of dollars, while also trying to use emotional and romantic manipulation.
The Iranian operator transferred funds to the Shin Bet operative using Bitcoins. The operator used business reasons as a cover story for the missions she assigned, including a request for revenge against those who owed her money, a desire to harm personal opponents and even a desire to harm LGBT people in general.
The Iranian operator also tried to get the Shin Bet operative she thought was working for her to put up signs inciting against Russian President Vladimir Putin in an attempt to harm relations between Israel and Russia.
The fake account operator also tried to gather intelligence and harm representatives of companies and diplomats from Arab countries working in Israel.
“This activity of the Shin Bet exposed Iranian practices alongside a desire to harm Israeli personalities and Israel’s foreign relations with various countries,” said the Shin Bet. “The Shin Bet, in accordance with its mission under the law, continues to act in the face of other similar moves by Iranians and terrorist organizations in cyberspace.”
The security establishment called on Israeli citizens to be vigilant and cautious in light of the threat posed by terrorist elements on social media, and to report any unusual contact to the police.
Terrorist groups, including Hamas, have often used fake Facebook accounts to target Israelis as they attempt to gather intelligence.
Last month, Cybereason reported that it had tracked two Hamas-affiliated groups that were targeting Israeli individuals with sophisticated social engineering techniques in order to deliver spyware to extract sensitive information from Windows and Android devices.
The Hamas groups used fake Facebook profiles to trick targeted individuals into downloading direct message applications infected with malware for Android and PCs.
